Bare Metal Hypervisors
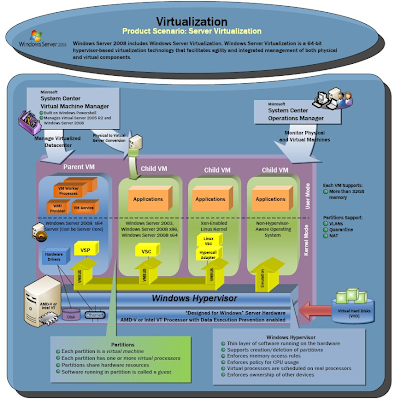
August 24, 2009 (Network World eEdition) - The phrase “bare-metal client hypervisor” is a mouthful, but one IT execs ought to get used to saying in the coming years. As the name suggests, this type of hypervisor sits directly on top of hardware--desktop computers, laptops, perhaps even smartphones one day--running independently from the operating system. Download a copy of Microsoft Hyper-V Server 2008 . “This is exciting technology,” says Chris Wolf, a senior analyst with Burton Group. “It provides enterprises with a tremendous amount of flexibility.” One desktop, multiple VMs One reason for his enthusiasm, Wolf says, is the ability to run multiple virtual machines (VM) on top of a bare-metal client hypervisor. A user machine takes on a whole new personality under this type of architecture. On a desktop computer outfitted with a client hypervisor, for example, you might find corporate-sanctioned and supported operating system and applications running on a locked-down VM. Personal appl



